Can PAM Coexist with the Zero Trust Security Model?

Joseph Carson
What is the zero trust security model and why was it introduced?
The concept of zero trust security isn’t new; the term was coined by Forrester Research Inc. back in 2010 and was initially synonymous with a network security approach known as micro-segmentation. Micro-segmentation is a way to create secure zones in data centers and cloud deployments that allow you to isolate workloads and protect them individually.
This approach is attractive because the traditional security perimeter was no longer proving effective at cybersecurity control. Fast-growing technologies, such as cloud, mobile, and virtualization, made the security boundaries of an organization blurry. For years organizations protected their valuable and sensitive data by building a fence around those assets, and all the data that flowed in and out was either via a single internet access point or on physical devices. This meant that a traditional perimeter was an effective measure as the boundaries were known and controlled.
As long as internet access was managed, it was possible to protect, monitor, and control the data that flowed through it.
If your users are accessing more IT services outside the security perimeter than inside, how protective can the perimeter really be?
Organizations protected internet access with firewalls, VPNs, access controls, IDS, IPS, SIEMs, email gateways, and so forth, building multiple layers of security at the so-called perimeter. On physical devices, systems management and antivirus protected those systems and kept them updated with the latest security patches. This traditional defense in depth security approach has been used for almost 30 years, but in today’s world, it’s no longer enough. If your users are accessing more IT services outside the perimeter than inside, how protective can the perimeter really be?
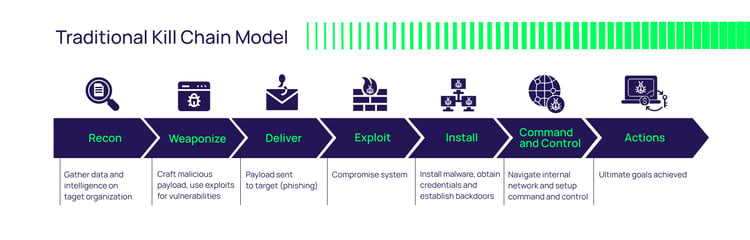
Trust, in the past, was something that we heavily relied upon. Once an employee had a corporate laptop and authenticated, they were then expected to do their job and not abuse the trust entitled to them. However, cybercriminals took advantage of that exact flaw in the security model by abusing trusted user identities and compromising their credentials to gain access to company systems and sensitive information under the guise of authorized employees.
Today, trust is being abused by cybercriminals targeting unsuspecting employees' personal accounts to gain access, later elevating to privileged accounts that can move around corporate networks undetected, and roaming around the network for months or even longer. Once attackers gain access to the internal network they typically have access to the entire network as everything inside the network is automatically trusted. This is why the zero trust security model was introduced—to address a new stance on trust: never trust and always verify.
Want to dive into the world of cybercriminals and their attack strategies? Go watch Delinea’s On-Demand webinar “Inside the Mind of an Ethical Hacker.”
How has zero trust evolved since 2010?
Security product vendors have been steadily jumping on the zero trust bandwagon since 2010 to the point that zero trust has ballooned to include almost every type of cybersecurity technology under the sun.
Forrester took a crucial step toward reigning in the definition of zero trust by publishing their inaugural Zero Trust Wave report: “The Forrester Wave: Zero Trust eXtended (ZTX) Ecosystem Providers, Q4 2018.” In the report, Forrester’s framework is based on technology controls and defines 7 controls that are the basic on-ramps of ZTX: network security, device security, identity security, application security, data security, security analytics, and security automation.
With zero trust having evolved beyond network security into the seven exclusive on-ramps we have today, businesses must choose carefully which ones to implement and when. Businesses have limited budgets to pursue these on-ramps, and of all the available on-ramps, identity security is the most efficient on-ramp at maximizing security as a vast majority of cybercrimes involve compromised credentials.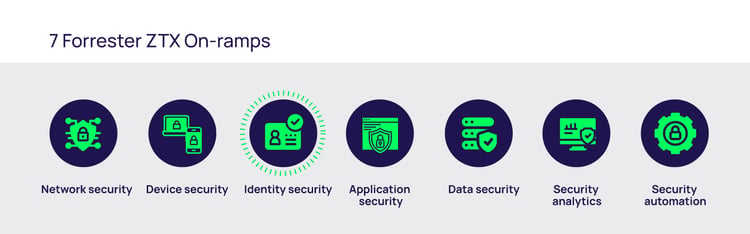
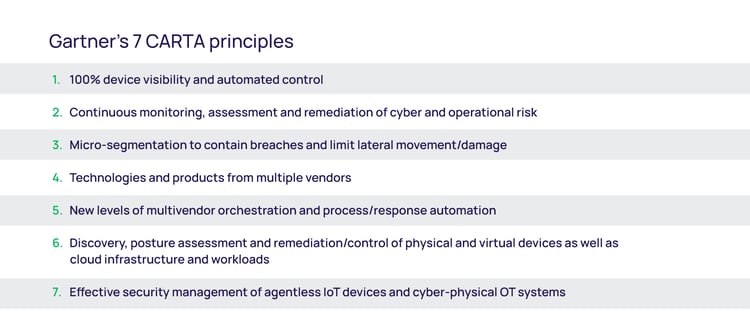
Gartner jumped into the zero trust conversation with their Continuous Adaptive Risk and Trust Assessment (CARTA) approach, and its “7 principles,” proposing that zero trust is only the first step in the process. CARTA is based on the balance between risk and trust; high-value assets represent business risk and, therefore, require a higher degree of trust from anyone trying to gain access.
Organizations that implement the zero trust security model quickly find that the model is opposite of how they have traditionally approached network security
The challenge with these approaches is that they’re so broad and comprehensive it’s difficult to know where to start. Where is your biggest risk? What do attackers see as the low-hanging fruit? What can you do to eliminate the most risk as quickly and affordably as possible? To add to the challenge, organizations that implement the zero trust security model quickly find that the model is the opposite of how they have traditionally approached network security. Switching from trusting everything to trusting nothing—and always verifying—has increased friction for employees and negatively impacts productivity.
Although zero trust is firmly associated with security, the truth is it breaks the balance between security and productivity. And it does so at a time when we need security to help the business to be productive and free of friction, enabling employees to do their jobs effectively and efficiently.
If you would like to learn more about the zero trust approach and how it will benefit your organization's security posture, I highly recommend you download our eBook: Zero Trust Privilege for Dummies.Our take on privileged access and its relationship to zero trust security
Delinea's approach to privileged access aligns well with the concept of zero trust and incorporates elements of both Forrester’s and Gartner’s approaches. The overarching zero trust concept of “never trust, always verify” is about controlling access—and privileged access is the riskiest type of access. It’s why Forrester estimates that 80% of security breaches involve misuse of privileged credentials.
Gartner ranked PAM (Privileged Access Management) as the #1 security project for 2019 because there are clear and effective steps you can take to reduce your privileged access risk. If you can control and monitor privileged access you’ll mitigate the most cyber risk in the shortest time.
How the zero trust security model works
Zero trust assumes any user or system that accesses the network, services, applications, data, or systems starts with no trust. To gain authorized access, trust must be earned by the prospective user through verification. For example, verification can require two-factor authentication. A user provides a password and must take an additional step by using an authentication application.
When new devices are introduced to the network, they must identify and verify themselves based on security controls before they can access resources. The more sensitive the resources to be accessed, the more security controls they must satisfy.
- Untrusted networks, devices, and BYODs should always be zero trust with continuous identity verification
- Trusted networks, devices, and users should start with zero trust, allow them to build trust, and revalidate when the security posture changes or the risks increase
However, zero trust should not be the final goal. It's an initial step to a dynamic or adaptive security model, such as the Gartner CARTA approach. In this model, when the threat is high, the security fence increases, and when the threat is low, the security fence automatically decreases. Managing this dynamic requires the efficient use of threat detection and intelligence to track activity.
By combining digital identity, multi-factor authentication, biometrics, behavioral analytics, and privileged access, you can build a dynamic security fence using a trust score or risk framework for digital identities. This dynamic security fence is designed to alert and/or challenge access when user behavior changes or becomes suspicious. Then you can use internal trust definitions to determine when security controls should be more sensitive.
For example, when a new variant of malware or ransomware emerges in the wild and exploits known vulnerabilities that have not yet been patched, dynamic security measures can increase security sensitivity. So, when a human or system detects a privileged access request from an unknown source, it can prevent access until additional security controls are satisfied, such as peer review or alternative approval workflows.
As such, privileged identity management (PIM) and adaptive security can continuously check trust levels, and when a user or system makes too many unusual or anomalous changes, the privileged identity management solution will automatically challenge additional identification of the human or system.

Zero trust challenges the traditional network perimeter defense architecture that relies on VPNs and firewalls. Zero trust requires multiple levels of granular access control and verification at system login and application execution to ensure individuals can only access the data and resources they need.
“Zero trust has an important role in improving security and reducing business risk but it’s only an initial step in this process.”
In this short video filmed at InfoSecurity Europe, I discuss cybersecurity and vendor relationships:
Zero trust is introduced at minute 3:02
Implementing PAM to achieve the principles of zero trust
Like Gartner, we recommend taking a risk-based approach to implementing zero trust security and Privileged Access Management. Forrester’s ZTX technology controls also provide a road map for key areas to address. The lowest hanging fruit in the PAM world and a great way to remove lots of risks quickly is by changing default IDs and passwords for built-in privileged accounts. This maps to the ZTX identity security control.
Another quick win that maps to the ZTX device security control is implementing least privilege controls on endpoint devices like laptops and workstations. Local admin accounts on these devices should be locked down, and any application or task that requires elevated permissions should only be granted access via workflow approval.
The next major area of risk to address is controlling privileged access to your most business-critical systems, applications, and data. This requires a combination of vaulting and server-level privilege elevation, and maps to the ZTX identity, application, and data security controls. It's important to determine which privileged accounts have access to these systems, who has access to those accounts, as well as the time and location of typical access.
For these high-risk accounts, keep the credentials in an encrypted vault so they can’t be shared or reused, use at least two-factor authentication to access the vault, rotate credentials frequently (if not after every use), and restrict the time and locations from which access is allowed. These vaulted accounts should only be used for emergency break-glass situations. For day-to-day administrative tasks, users access systems with their low-privilege individual accounts. Privilege elevation on the server controls what privileged applications and commands the user can execute. Combining privilege elevation with MFA on server login, as well as elevation and access request workflows helps drive down risk further.
Because attackers often try to create new privileged accounts in order to move laterally and avoid detection, you need to strictly control the process that governs how and why new privileged accounts are created. This maps to the ZTX security automation control.
All privileged account activity for critical systems should be monitored and recorded. This can be done at the vault/proxy level for sessions initiated from the vault. In case a cybercriminal circumvents the vault—for example, a knowledgeable insider—session recording on each server is necessary to ensure full visibility. This maps to the ZTX security analytics control. Users are encouraged to follow the rules when they know their behavior is being monitored. Recorded session data is invaluable when investigating the cause of a breach.
Classifying trust dynamically and making it adaptive to business risks
Cybersecurity classifications of trust and accepted risk should be adaptive. This means you must create policies or rules across the enterprise for identities, services, applications, data, and systems. For example, you can “always verify” and “always monitor” policy for third-party vendors or contractor identities. Internal employee classifications are adaptive based on the sensitivity of the data being accessed. An “always verify” policy would require credentials and multi-factor authentication, while an “always monitor” policy would audit and record all activity.
Moving beyond zero trust to adaptive risk-based security
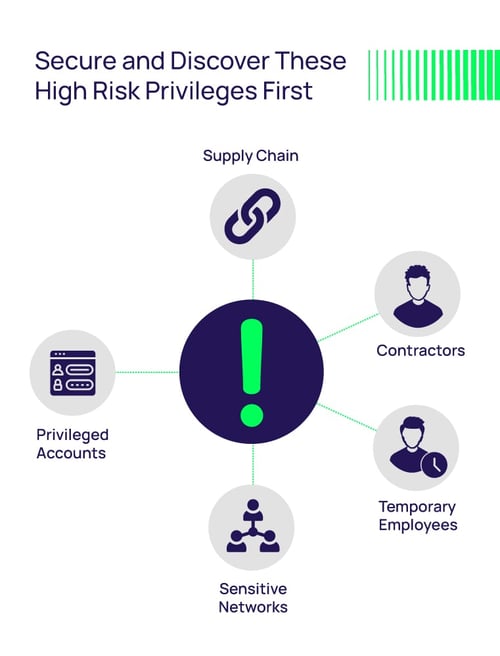
Zero trust is about ensuring that only appropriate access is granted to critical assets. Organizations typically start their journey to zero trust security by prioritizing high-risk areas, such as supply chain, contractors, temporary employees, sensitive networks, and privileged accounts. This initial step helps reduce the risk of attackers abusing accounts that may have less security or visibility.
Zero trust is the baseline from which organizations can build trust scores they can use to determine how much security is required for appropriate access to internal networks and systems. This concept can be applied and enforced broadly for the entire network and all its assets. Depending on the level of security and control needed, zero trust controls can also be implemented specifically, creating different levels of trust and verification at the micro-segment or individual asset level.

FREE EBOOK
Decrease your risk of a breach with a modern PAM solution founded on zero trust principles



