INCIDENT DETECTION AND RESPONSE
Privileged Behavior Analytics
Detect anomalies in privileged accounts across your network.
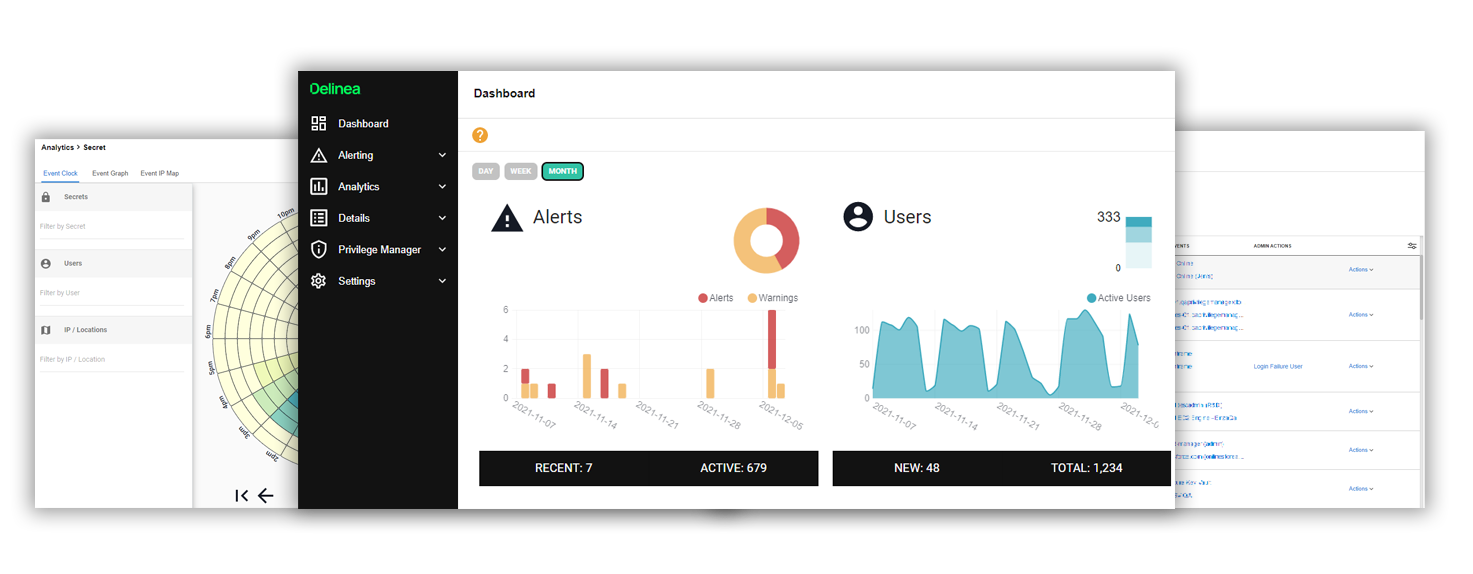
Know the warning signs of privileged account abuse
Sudden increase in privileged account access by certain users or systems
Atypical access of the most privileged accounts or secrets
High number of privileged accounts accessed at once
Accounts accessed at unusual times of day or locations
“Privileged Behavior Analytics saves admins the hours of manual labor that would be required to sort through thousands of logs to find evidence of unusual behavior, at which point attackers are generally long gone.”

Detect early signs of a breach
Privileged Behavior Analytics can quickly detect this anomalous behavior and instantly alert your security team to a cyber attack or insider threat before a breach catastrophe happens.
Privileged Behavior Analytics
Delinea Privileged Behavior Analytics uses advanced machine learning to analyze activity on privileged accounts in real-time to detect anomalies and provide threat scoring and configurable alerts.
Advanced machine learning analyzes all privileged account activity so you can spot problems and measure the extent of a breach.

Download the Privileged Behavior Analytics datasheet
Reducing security risks to your organization by improving security saves your department time, money, and resources and maximizes your current investment in Secret Server and Privilege Manager.
Try it Free Now
Privileged Behavior Analytics supports extended PAM
The standard definition of PAM isn’t sufficient for the growing risk of cyberattacks. We believe PAM must address the exploding number of identities and today’s IT complexities.
Our products provide effective authorization controls for an identity-centric approach to security.
Enable swift and effective incident response
PBA imports all secret and user history from Secret Server
When risk scores pass acceptable thresholds you’re instantly alerted so you can protect privileged accounts by immediately rotating passwords, requiring additional authentication, or increasing session monitoring. PBA connects seamlessly to your security and IT software. It can automatically take action in Secret Server, send alert notifications in Slack or open a ticket in ServiceNow.
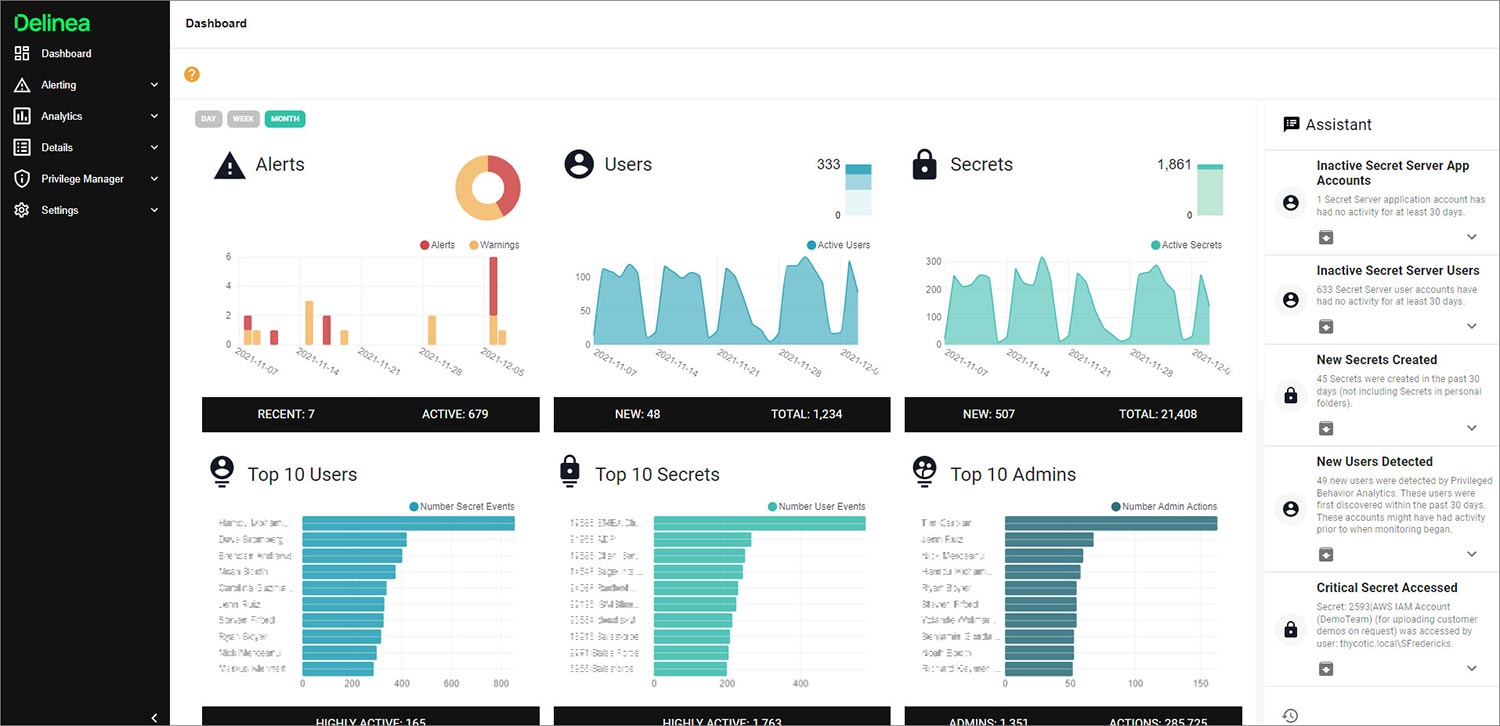
Gain insight into endpoint privilege management
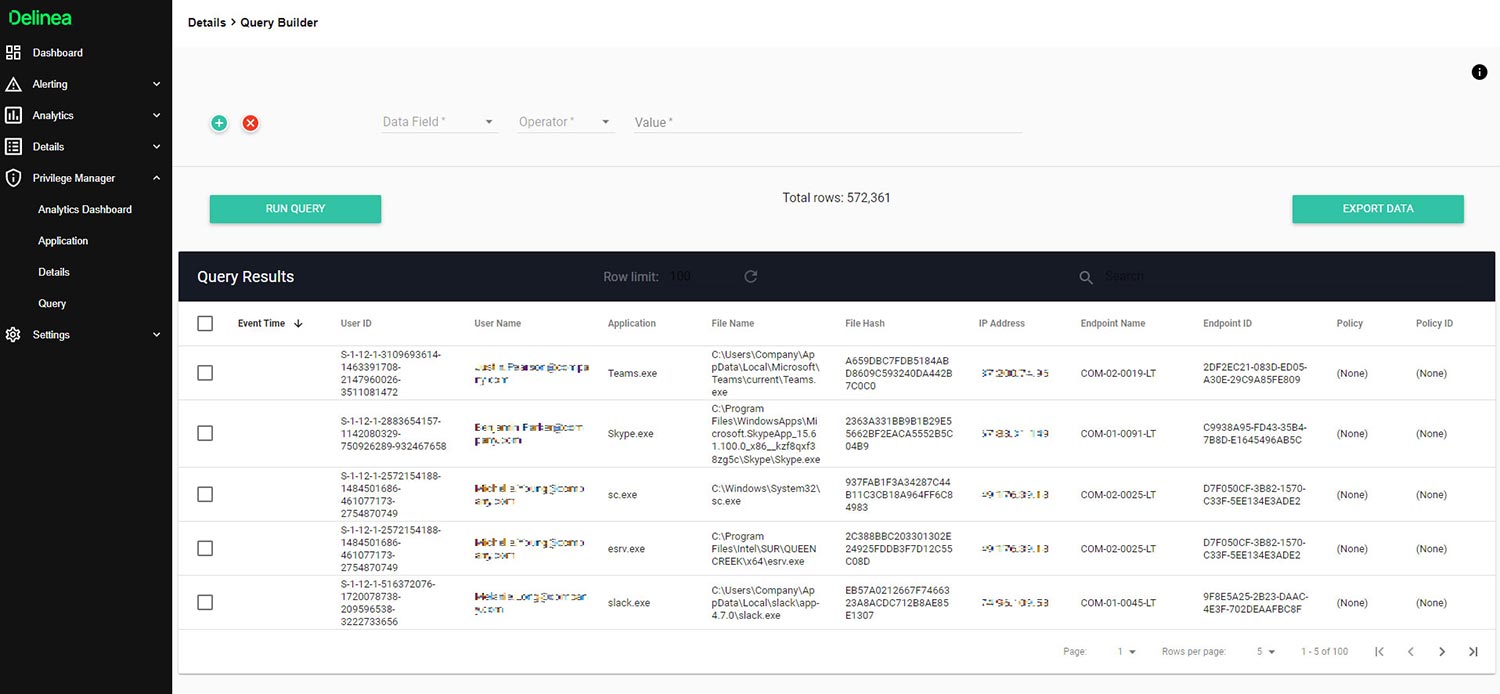
Privilege Manager Cloud sends endpoint-related data to Privileged Behavior Analytics for advanced analytics and guidance on what applications need to be addressed by policies. Use the dashboard to see top users and applications per day, month, or year. The query builder provides easy custom reporting on Privilege Manager endpoint and application data.
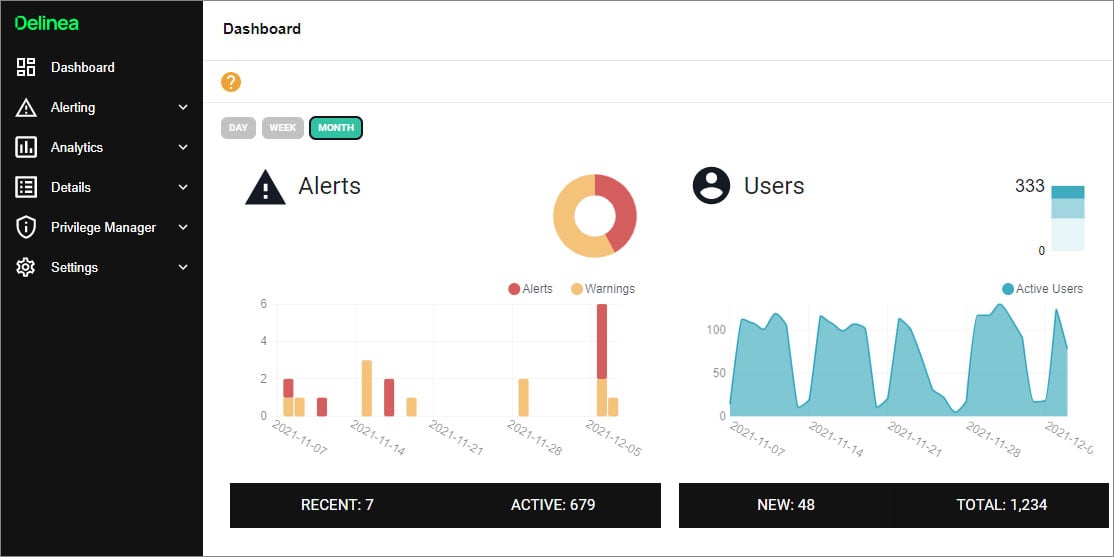
At-a-glance dashboard and actionable reports help you cut through the noise to see what’s most important
Easy-to-Manage Controls and Reports- Detailed snapshot of privileged account activity
- Real-time behavior pattern recognition
- Threat scoring to prioritize issues
- Map view of privileged users and related accounts
- Controls to manually increase sensitivity for specific users or accounts
- Configurable alerts

When disaster strikes how quickly can you respond?
Make sure your incident response plan protects privileged accounts.
IT operations, security and incident response teams must form a united front against cyber attacks to coordinate actions and maintain business continuity. That takes tools like PBA and an effective incident response plan.
Download a free Disaster Response Template to get you started!
