Cybersecurity Resources
Learn to protect your most critical systems and data with these free, in-depth PAM and IT Security resources. Search our library of webinars, videos, whitepapers, case studies, and more to get started with Privileged Access Management, get the most from Delinea’s solutions, and hear inspiring stories of PAM success from companies just like yours.
Looking for something specific? Search here:
Datasheet

Privilege Management for Workstations
Whitepaper

2024 CyberEdge Cyberthreat Defense Report
Free Tool

PAM Journey Assessment Mapping Tool
Demo
Remote Access Service Interactive Demos
Video

Seamless Privileged Access Control across all identities
Demo
Privilege Control for Servers Interactive Demos
Datasheet

Protect Servers with Privilege Control
Whitepaper

2024 State of Ransomware Survey and Report
Whitepaper

Mapping the NIST Cybersecurity Framework 2.0 to Delinea PAM
Case Study

Delinea builds trust to support AD&C's digital transformation
Video
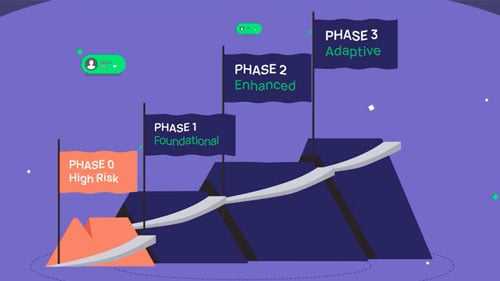
Delinea PAM Maturity Model Overview
Demo