Zero Trust
What is Zero Trust and Zero Trust Extended (ZTX)?
Zero trust redefines legacy Privileged Access Management (PAM) for the modern enterprise IT threat landscape. Organizations must discard the old "trust but verify" model, which relied on implicit user trust plus well-defined boundaries. Zero trust mandates a "never trust, always verify, enforce least privilege" approach to privileged access from inside or outside the network.
Zero trust requires granting least privilege access based on verifying who requests access, the request's context, and the access environment's risk. By implementing least privilege access, organizations minimize the attack surface, improve audit and compliance visibility, and reduce risk, complexity, and costs for the modern, hybrid enterprise.
What about ZTX?
In 2017, Forrester gave Zero Trust a refresh resulting in Zero Trust Extended (ZTX). They made it more prescriptive to facilitate implementation. ZTX accounted for business transformation and advances in technology-driven mainly by cloud adoption. They expanded the framework beyond network segmentation into a complete and holistic approach, including:
- Data
- Networks
- People
- Workloads
- Devices
- Analytics
- Automation
This extended framework now gives organizations alternative "on-ramps" to achieve Zero Trust based on their risk-mitigation agendas. The on-ramp that best represents the use of PAM to address identity-related risk is the "People" pillar. Zero Trust for People focuses on governing and enforcing security controls during authentication and authorization. I.e., during login to workstations, servers, and network devices and when executing privileged applications and commands to prevent data breaches and ransomware.

Decrease your risk of a breach with a modern PAM solution founded on zero trust principles
Legacy PAM is not enough for the expanded threat landscape
Legacy PAM has been around for decades and was designed back in the day when ALL your privileged access was constrained to systems and resources INSIDE your network. The environment was systems admins with a shared "root" account that they would check out of a password vault, typically to access a server, a database, or a network device. Legacy PAM served its purpose.
However, today's environment is different. Privileged access not only covers infrastructure, databases, and network devices but is extended to cloud environments. It also includes Big Data projects, must be automated for DevOps, and needs to accommodate hundreds of containers or microservices to represent what used to be a monolithic app on a single server.
We all live in a world of Advanced Persistent Threats (APTs) that create a growing risk to organizations' financial assets, intellectual property, and reputations. For most APTs, such as ransomware, expanding access and obtaining credentials is a crucial tactic, with privileged access ideal.
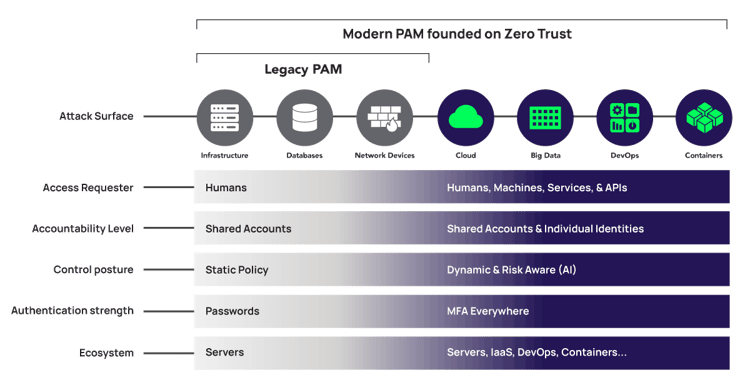
The shift from Legacy Privileged Access Management to modern PAM founded on zero trust
Modern PAM, founded on zero trust, is designed to handle requesters that are not only human but also machines, services, and APIs. Shared accounts will persist, but for increased assurance, best practices now recommend using individual identities, not shared accounts, where we can enforce least privilege.
All access controls must be dynamic and risk-aware, requiring modern machine learning and user behavior analytics. PAM must integrate and interoperate with a broader ecosystem, including IaaS providers like AWS and Azure, with DevOps CI/CD pipeline tools such as HashiCorp and Ansible, and container solutions such as Docker and Kubernetes.
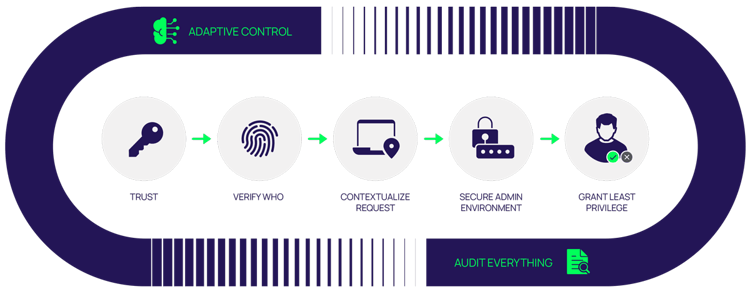
The zero trust approach
A zero trust approach helps enterprises grant least privilege access based on verifying who is requesting access, the request's context, and the access environment's risk. Doing so minimizes the attack surface, improves audit and compliance visibility, and reduces risk, complexity, and costs.
We can distill a zero trust model into six tenets, covered in detail below:
1. Trust
![]()
As PAM discovers servers in your extended enterprise, they are enrolled in the PAM service establishing a trust relationship. Just as we strive to validate the legitimacy of human admins, we also need to verify the legitimacy of our servers and the PAM service itself. So, when the server receives PAM policies to control login, privilege elevation, and MFA—the server can trust these policies come from a legitimate source and not a rogue service.
And vice-versa, say on the server, a DevOps application needs to check out a vaulted Secret through an API call—the PAM service can similarly validate that the request is from a trusted source. This trust relationship is established during the enrollment process.
2. Verify Who
![]()
Today, identities include not just people but workloads, services, and machines. Verifying who means leveraging enterprise directory identities, eliminating local accounts, and decreasing the overall number of accounts and passwords, reducing the attack surface.
Many large organizations have standardized on Microsoft's Active Directory (AD) or OpenLDAP for employees. Cloud transformation has led many to migrate to cloud directories such as Azure AD, Ping, or Okta. Zero trust doesn't limit or constrain you to a specific directory. You can keep different populations of identities in other directories.
To align with zero trust and least privilege, administrators routinely use their low-privilege individual enterprise ID for access and elevate rights just-in-time for privileged tasks. Some organizations subscribe to a Microsoft best practice that assigns a secondary "Alternate Admin" or "Dash-A" account specifically for privileged tasks. This account ID is private (i.e., not on a business card) and cryptic (i.e., not easily extrapolated from the public account ID). Thus, if a cybercriminal compromises the public email account, it does not expose their Alternate Admin Account.
To verify, Multi-Factor Authentication (MFA) plays a critical role in assuring the user's identity. We must determine if there's a human at the keyboard and if the requestor is the legitimate owner of that credential. Also, MFA should be enforced at all access control gates, such as vault login, password checkout, server login, and privilege elevation.
To mitigate the risk of a compromised credential being used to affect a data breach, best practices for MFA include phishing-resistant authenticators such as a FIDO2 dongle. The National Institute for Standards and Technology (NIST) publishes recommendations for various Authenticator Assurance Levels (AAL) that provide increased confidence and strength. AAL2 should be a minimum for admin functions.
This means a dual challenge: something you know and something you have. A good example is a password combined with a push notification to your phone or an OTP generated by your phone. For most critical assets, AAL3 is preferred. This is a password plus a hardware-based cryptographic token, such as a smart card or FIDO key. Google claims they have not had a single successful phishing attack since they implemented FIDO keys for all users as part of their BeyondCorp zero trust initiative.
3. Contextualize Request
![]()
With zero trust, we remove implicit trust in our admins to support a least privilege model and continuous verification. They have minimal rights but with the means to request elevated privileges, just-in-time, via self-service workflows built-in to the PAM solution or a 3rd-party such as the ServiceNow Help Desk.
However, approval without sufficient context can result in increased risk. Thus, context ensures an informed grant/deny decision. Context includes information such as a role, the target server, for how long the user needs access, a typed rationale for why it's needed, and a trouble ticket number.
Granular roles help further mitigate risk by assigning only necessary rights. Granting broad rights exposes sensitive systems, apps, and data beyond what's essential for the task and gives cybercriminals a leg-up on their attack plan.
4. Secure Admin Environment
![]()
In its privileged access strategy, Microsoft refers to this as a "Clean Source." A goal is to isolate our sensitive internal systems from whatever is accessing them remotely. Doing this and avoiding VPN connections helps protect our business-critical servers from several forms of risk.
One is the risk of a remote user's workstation spreading malware or a virus, especially for outsourced IT and 3rd-party contractors. Here, we have limited, if any, control over that device to ensure it's clean. Another risk is a VPN and jump host not supporting granular access control and giving a user visibility and access to servers in the network beyond the one they're authorized to touch. Finally, there's the risk of an external threat actor gaining network and server access via a compromised VPN account.
Secure VPN-less remote access mitigates all these risks. There's no VPN account to compromise and exploit. Zero trust means preventing direct access from user workstations that are too easily infected with malware and having access to the internet and email. The user workstation is not network-attached, so it can't spread any infection that may be present on the device. Zero trust means surgically placing the user on the target server and preventing illicit lateral movement.
The beauty of a properly designed zero trust architecture is the combination of security and productivity. It provides easy browser-based access for remote internal and third-party users without requiring client software. RDP and SSH access from anywhere, anytime, to servers on-premise or in multiple clouds, VPCs, and VNets.
5. Grant Least Privilege
![]()
The Principle of Least Privilege (PoLP) is a well-established security best practice. With least privilege at the core of a PAM solution founded on zero trust, this establishes a model of just enough privilege, granted just in time for a limited time. PoLP helps break the attack chain at multiple places, including the workstation and servers.
The workstation is a bigger target than ever due to the remote workforce. It's typically the first step in a kill chain where account takeover, workstation compromise, privilege escalation, and vertical movement to the server network is a common approach. On the server, privilege elevation and lateral movement is another common tactic leading to data exfiltration or encryption for ransom. Least privilege breaks the kill chain at the workstation and server levels, preventing privilege escalation and vertical and lateral movement.
6. Audit Everything
![]()
For privileged sessions, it is best practice to audit everything. With a documented record of all actions performed, we can use audit logs during an audit in forensic analysis to find the root cause and to attribute actions taken to a specific user for full accountability.
Because privileged sessions are so critical, it is also a best practice to capture a video recording of the session for proof that controls are in place and doing their job or used as evidence during an investigation. Multiple regulations, including PCI-DSS for payment card data, specifically require this level of auditing.
Live session auditing and recording are commonly done through a gateway or proxy, for example, a vault proxy, when users establish sessions via the vault. However, a clever cybercriminal may circumvent the vault, so doing this also at the host level covers your bases. It also provides additional operating system-level granularity, such as capturing individual commands executed from within a batch file or the actual commands hidden inside an alias.
If you have a security department, a good practice is to integrate this audit data with your existing Security Information and Event Management (SIEM) system or Cloud Access Security Broker (CASB) service for automated mining where risky activities can be identified, and alerts raised.
7. Adaptive Control
![]()
Adaptive control helps us distinguish friend from foe. It can be tough to detect and respond when a cybercriminal presents a valid user credential to log in to a server. It's even more complicated when a valid user has gone rogue, using their valid credential.
Zero trust controls are adaptive to the risk context to mitigate these risks. Contextual factors of a cybercriminal masquerading as a legitimate user will be inconsistent with the actual user. Context may include common attributes such as time of day, day of the week, location, IP address, target server, target application, using a trusted device, etc.
Static rules are used in this approach. However, they require human care and feeding. They're often stale, don't cover all possible bases, and can have a high false-positive rate.
Augmenting this with machine learning and behavioral analytics takes this to the next level. Such technology can consume and analyze millions of audit events in a fraction of a second, continuously looking for that needle in a haystack, which would never be achievable by manual forensics. Even more valuable is applying this inline in real-time during an access request for truly adaptive preventive controls versus after-the-fact detective controls.
Conclusion
Legacy PAM was the right solution for the right time.
To deliver zero trust for modern enterprises, PAM solutions must be cloud-native and designed to accommodate current hybrid cloud dynamics. Key characteristics include a solid blend of vaulting plus privilege elevation to enforce least privilege and break the attack chain at multiple points; just-enough access, just-in-time, for a limited time; MFA everywhere; and an easy browser experience to streamline remote access for internal users and third parties.
Want to learn more about how zero trust cybersecurity can protect your organization? Join Delinea's Chief Security Scientist Joe Carson in this 401 Access Denied podcast. Joe and Dave Lewis, Global Advisory CISO for Cisco, discuss the origins of Zero Trust and the steps you can take today to reduce your risk:
More zero trust resources:
Blogs
Just-in-Time (JIT) access series part 3: Zero Standing Privileges
Five best practices for zero trust security
Zero Trust for ICS/SCADA Systems
Top 3 PAM features that set Delinea zero trust privilege apart for cloud migrations
Free eBooks
Zero Trust Privilege for Dummies
Whitepaper
The Path to Zero Trust Starts with Identity
